Dealing with regulation; audit and compliance in SQL Server
In Foundry – Redgate’s research division – we’re focused on exploring new products and technologies for the Microsoft data platform. Over the last few months, we’ve been taking a close look at the problems people face when auditing and meeting regulatory compliance for SQL Server.
An introduction to compliance and SQL Server
Our research has given us some interesting problems to explore and we’d like to get your input: you can help us out and influence what we do next by filling in this survey (and being in with a chance to win $100), or having a look at our prototypes.
What’s it like to be audited?
We’ve been out and spoken to people around the world who are working to achieve and maintain compliance; database professionals, internal compliance managers and external consultants. During these conversations, we’ve heard about a plethora of regulations in great detail.
We’ve learned about security standards (including ISO27001 and PCI-DSS), about auditing accountability (such as SOX and JSOX), about financial regulatory frameworks (like BASEL3), and about regulations for handling personally identifiable information both generally (GPDR), and in healthcare (HIPAA and IG).
And through all these conversations we’ve come to understand that there’s not a great deal of built-in support for people working on the Microsoft data platform carrying out these audit and compliance activities.
We’ve identified six activities that Redgate could help with, and produced an interactive concept to illustrate a potential solution for each.
Audit and compliance activities
Trace user access to resources and data
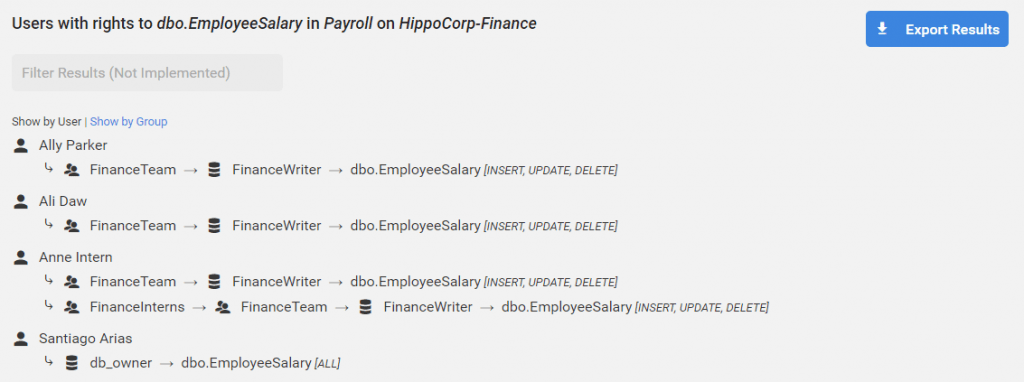
This feature demonstrates tracing access to a database object across the Active Directory boundary and results in the generation of a PDF report – a common exercise and form of evidence produced during an audit. Try the user access trace demo.
Discovering unsatisfactory server configuration and patch level
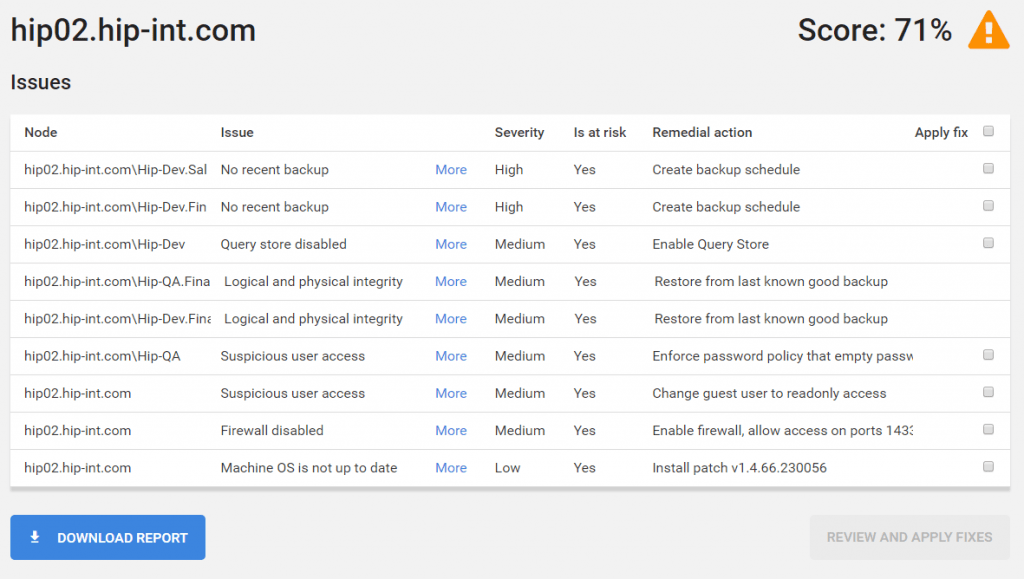
The state of both the SQL Server and the machine that it’s running on can change over time or become stale. While querying and maintain a single instance can be relatively straightforward, keeping on top of multiple instances and servers can be difficult. Try the server configuration compliance demo.
Fast and thorough alerting for security issues
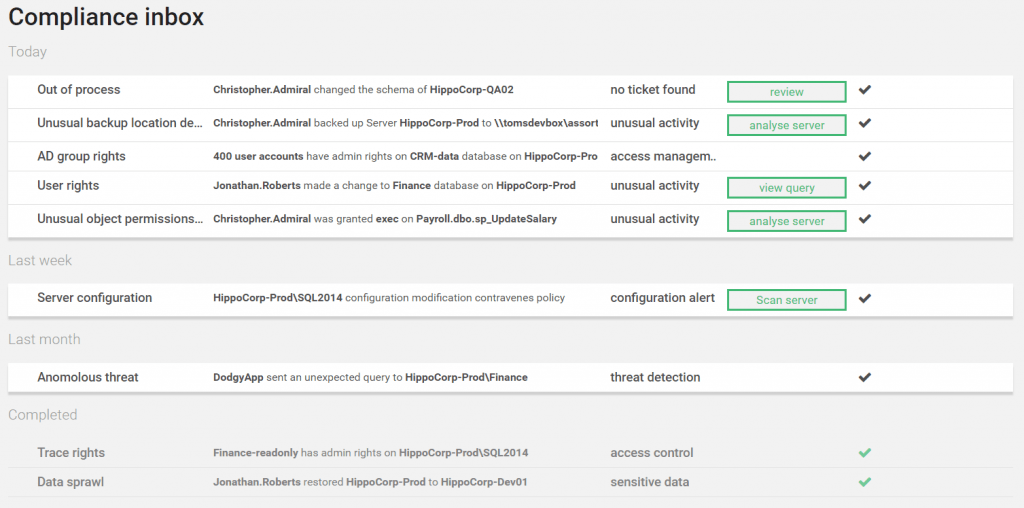
Even when you have policies in place, it can continue to be a challenge to keep on top of the changes that may undermine your compliance. The compliance inbox actively monitors your resources for events that compromise compliance. Try the compliance alert demo.
Protecting against the spread of personal data within your organization
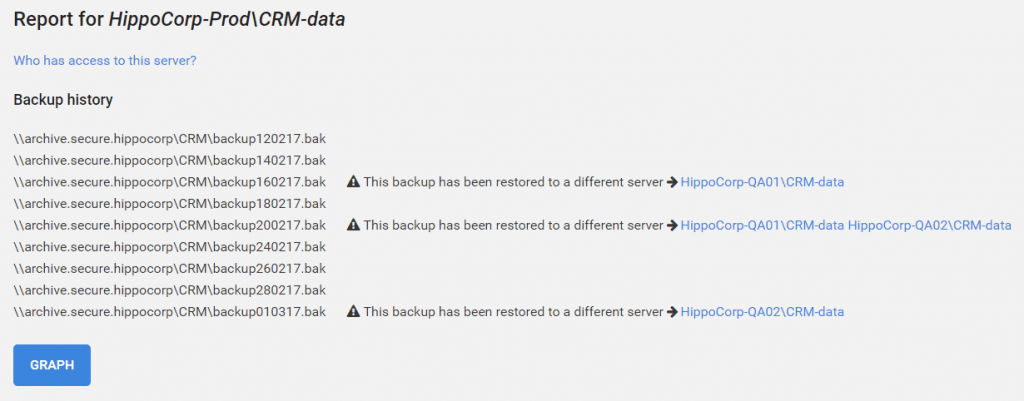
Full production backups are integral to database administration, but once created they can take on a life of their own. Tracking the lifecycle of backing up a database to a fileshare, restoring it to different servers and then backing it up again is not easy. Try the production data protection demo.
Detect and audit out-of-process changes
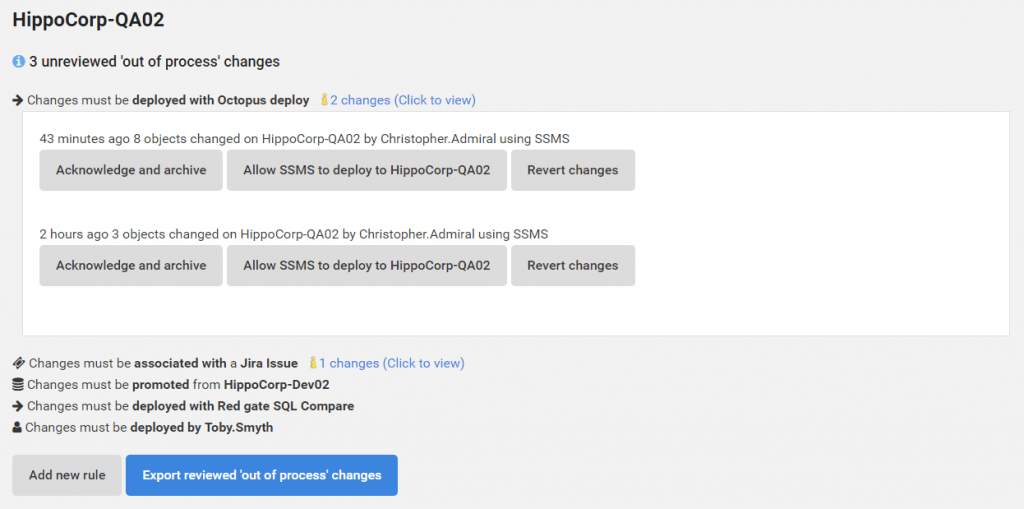
A well-documented and understood change management process can fall down when urgent work items need to bypass certain stages. Tying this work back to individual work items when auditing at a later stage can be difficult and time consuming (searching JIRA for matching timestamps, etc). Try the demo for detecting out-of-process changes.
Detect unauthorized or suspicious activity
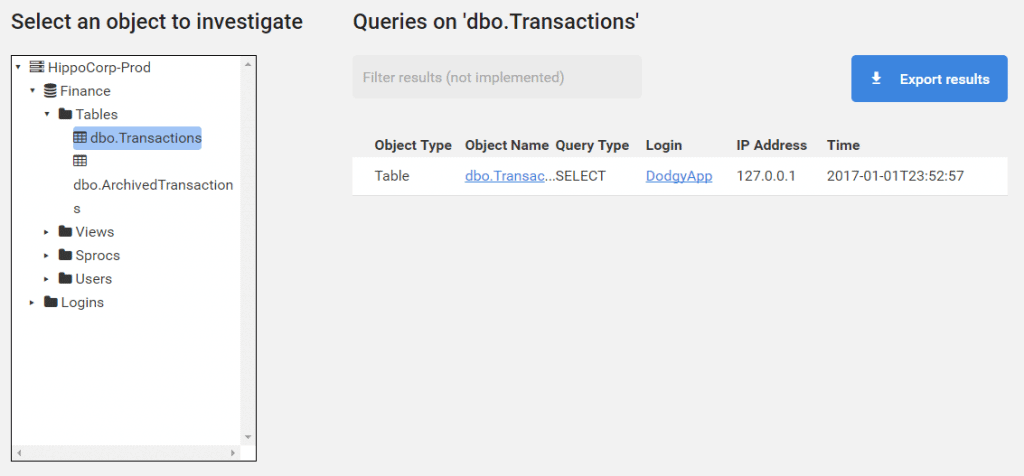
When audit logs are large, it’s difficult to report on all the activity (see what data was accessed and when), let alone pick out anomalous behavior. Try the SQL query capture demo.
Tell us about your audit experience and win $100
We’d really like to hear about your experience with audit and compliance activities in SQL Server. Complete our survey and leave your details to be in with a chance of winning an Amazon gift card worth $100 (or the equivalent in your preferred currency).
Complete the survey to enter the draw. (The survey closes 30 April 2017, and the draw will take place on 1 May 2017.)
About Foundry
Foundry is Redgate’s product research and development division. Based in Cambridge, UK, we’re responsible for delivering the newest products and technology for professionals using the Microsoft data platform. You can find out more about the Foundry team and what it does on our web page, where you can also keep up to date with the latest projects and prototypes, or contact us if you’d like to talk to the team about your audit and compliance projects.