What is the Essential Eight Maturity Model – and where does your data fit into the picture?
Join any conversation about cybersecurity in Australia and the Essential Eight Maturity Model may well be mentioned. Introduced in 2017 by the Australian Cyber Security Centre (ACSC), its purpose is to help non-corporate Commonwealth entities (NCEs) minimise the risk of cyber attacks by following eight mitigation strategies in three key areas:
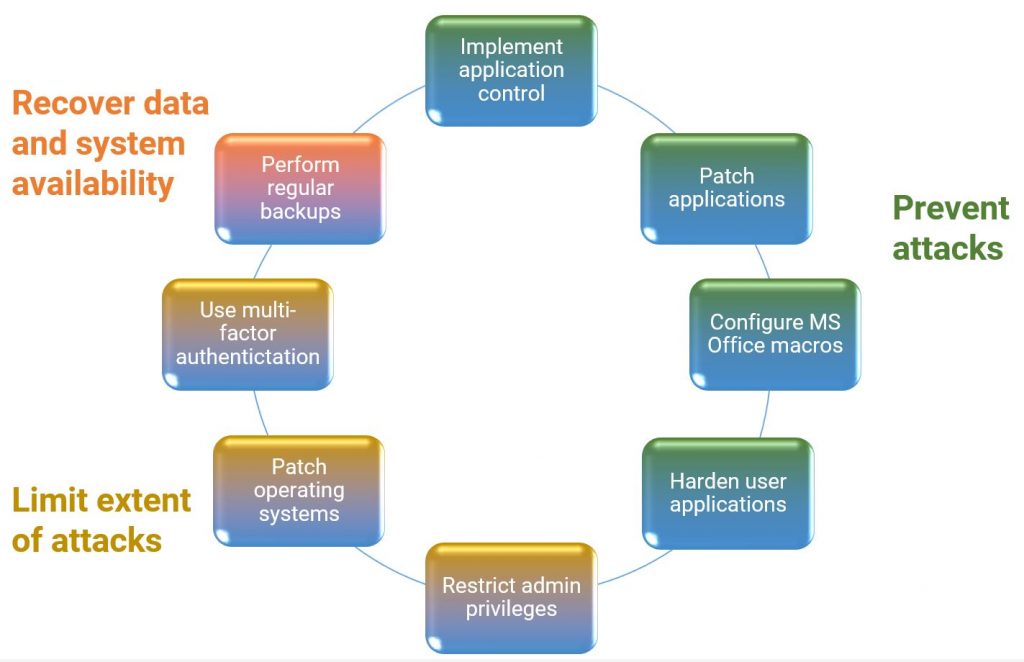
The risk management framework it presents provides actionable advice for any organisation to follow, whether they’re an NCE or not, when protecting Microsoft Windows-based internet-connected networks.
Four of the mitigation strategies – application controls, patching applications and operating systems, and restricting admin privileges – have also been mandatory for NCEs since 2013 under the Protective Security Policy Framework (PSPF).
Commonly referred to as the Top Four, these are naturally the focus for NCEs in their cyber security planning. Fair warning here, however, because this is likely to change. The Attorney-General’s Department (AGD) was asked in December 2020 if it was possible to make all of the Essential Eight mandatory under the PSPF. The AGD published an Executive Minute in response in June 2021, which stated:
The department has carefully considered … and has held detailed discussions with the ACSC on the cyber security settings in the PSPF. On this basis, the department will recommend an amendment to the PSPF to mandate the Essential Eight.
This reflects the ACSC’s advice that entities should progress maturity across all 8 strategies that form part of the Essential Eight, rather than focusing efforts on a smaller subset like the Top Four, as this provides a greater level of protection.
So if you’re an NCE and the Essential Eight has been on the back burner while you concentrate on the Top Four, it’s time to move up a gear. Fortunately, the ACSC has made it easier by publishing guidelines on how to implement the Maturity Model.
The guidelines show how the mitigation strategies can be achieved by moving from a basic Level One approach to a more comprehensive Level Three approach. Importantly, an October 2021 update to the Essential Eight Maturity Model recommends that NCEs and other organisations which follow the model should do so level by level. Rather than having some mitigation strategies at Level One and others at Level Two or Three, NCEs should plan to achieve the same level across all eight strategies before moving onto the next.
More tellingly, there are now four maturity levels based on mitigating the increasing sophistication of the tools, tactics, techniques, procedures and targeting used by adversaries. The key is to determine the right target maturity level to implement, based on the type of adversaries the NCE will be likely to face. A large part of this will be down to the confidentiality and sensitivity of the data that is collected, processed and stored, along with how important it is for the systems and data to be uninterrupted and available.
The base level, Maturity Level Zero, is where there are weaknesses in the overall cyber security posture which any adversary, even unskilled ones, could use to compromise the confidentiality of data and the availability of systems. Levels One, Two, and Three, introduce strategies and approaches which can then be used to address the threats posed by adversaries using opportunistic, tradecraft, or extreme techniques.
In broad terms, Maturity Level One is probably suitable for small to medium enterprises, Maturity Level Two is aimed more at large enterprises, and Maturity Level Three is generally appropriate for critical infrastructure providers and other organisations operating in high threat environments.
Rather than hindering or getting in the way of cyber security efforts, the Essential Eight Maturity Model offers a logical route for them to follow. It also enables NCEs and other organisations to make an informed business case to secure the funding for a cyber security initiative because the model details the steps that need to be taken to make it happen.
Er, what about the data?
While performing daily backups in order to recover data and system availability is one of the measures in the Essential Eight, the other seven mainly focus on preventing attacks and limiting their extent through heightened network and perimeter security.
That’s because the purpose of the Essential Eight, stated in the Introduction to the Maturity Model, is: ‘To help organisations protect themselves against various cyber threats.’ (My emphasis.) The Implementation section goes on to state:
While the Essential Eight can help to mitigate the majority of cyber threats, it will not mitigate all cyber threats. As such, additional mitigation strategies and security controls need to be considered, including those from the Strategies to Mitigate Cyber Security Incidents and the Information Security Manual.
The purpose of the Cyber Security Principles outlined in the Information Security Manual (ISM) is: ‘To provide strategic guidance on how organisations can protect their systems and data from cyber threats.’ (Again, my emphasis.)
This is an important distinction to make because there are two objectives of a cyber attack – to disable or destroy systems, or to manipulate or steal the data in those systems. So following the Essential Eight may help to mitigate the first objective, but it’s not enough to meet the second.
This is also at a time when cyber attacks are increasing, as are the severity of those attacks from a growing number of adversaries from both criminal and state actors. The 2020-2021 Annual Cyber Threat Report from the ACSC, for example, shows that over 67,500 cybercrime reports were received in that financial year, up nearly 13% from the previous year.
Hence the importance of thinking about the Cyber Security Principles from the ISM as well. They are grouped into four activities, many of which cover similar ground to the Essential Eight: Govern, Protect, Detect, and Respond.
The fifth Protect principle, for example, is to ensure security vulnerabilities in systems and applications are identified and mitigated in a timely manner. This is already covered in the Essential Eight requirement to patch applications and operating systems within two weeks of release, or within 48 hours if an exploit exists.
There are three other Protect principles, along with one of the Govern principles, which should be considered and addressed when planning how to protect the data within systems as well as the systems themselves:
- Govern principle 2: The identity and value of systems, applications and data is determined and documented.
- Protect principle 7: Data is encrypted at rest and in transit between different systems.
- Protect principle 10: Only trusted and vetted personnel are granted access to systems, applications and data repositories.
- Protect principle 11: Personnel are granted the minimum access to systems, applications and data repositories required for their duties.
In many ways, the identification and encryption of data, and the restriction of access to it, is the last – and best – line of defence against a cyber attack. It means that, even if one occurs, and a data breach happens, the damage will be minimal.
How Redgate can help
Redgate offers a complete portfolio of database development tools that enable the database to be included in DevOps practices and processes while keeping data safe. They also integrate with and plug into the tools already in use for application development, and enable you to meet the obligations of the Essential Eight as well as the Cyber Security Principles.
Redgate Monitor, for example, provides an instant overview of every version of SQL Server in use, along with the latest patches available, as well as the date and time of the last backups.
SQL Data Catalog accelerates the identification and classification of sensitive data, so that you know which data needs to be protected from breaches.
Data Masker can enhance your security further with an automated masking approach that encrypts data and makes it inaccessible to anyone, even when a data breach occurs.
SQL Provision enables software teams to deliver masked database copies for use in development and test environments, which speed up development yet ensure the security of sensitive data and minimise access to data repositories.
For more information about how Redgate can help you meet the requirements of the Essential Eight and the ISM’s Cyber Security Principles, visit our dedicated Australian Government solution pages online.
Read next
Blog post
Notifiable Data Breaches – and how to avoid them
With the significant growth of data across organizations and the increase in regulations everywhere aimed at protecting that data, the words ‘data breach’ aren’t something any organization wants to hear. That’s the message we often hear in conversations with customers. That said, I thought it would be good to share some insights on what data
Blog post
A quick guide to the New Zealand Privacy Act 2020 for DBAs
December 1 saw the introduction in New Zealand of the Privacy Act 2020 which not only brings increased protection for individuals but also has some new implications for businesses, including increased fines for non-compliance and the reporting of serious privacy breaches. However, the changes and impact may be less than organizations fear because the act

