SQL Clone and backups protected with TDE – part 2
Steve Jones proves that SQL Clone can create a clone from a TDE-protected SQL Server database backup.
My last article demonstrated that you can use SQL Clone to make a copy of a live database, even when that database is protected with Transparent Data Encryption (TDE).
However, not everyone will want to use SQL Clone against a live database, especially a production database. Fortunately, SQL Clone allows you to build an image from a backup file.
How does this work with a TDE-encrypted backup? Let’s take a look.
Building a data image from a TDE-protected database backup
The first step in building a SQL Clone database is to create an image. When I choose to create an image, I get this:
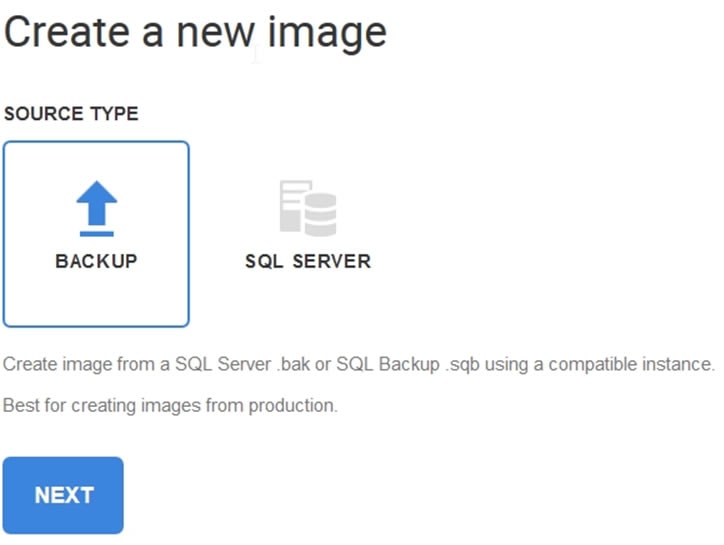
Figure 1
In the last article, we used a SQL Server database to create the image. In this one, let’s choose a backup. We’ll walk through the process of creating a data image from a TDE-protected backup, once creating the image on the same instance as the TDE-protected source database, and once creating the image on a separate instance.
Creating a data image on the same instance
First, we need to specify the backup location. I’ve previously added a folder, but you can easily click New Backup Location to pick a new one. This is a folder to which the SQL Clone Agent service has access.
Once I’ve specified the location, I need to specify a SQL Server instance, as SQL Clone needs to create a temporary database on this instance in order to restore the backup. In essence, the process of restoring the backup is what creates the data image. I’ll choose my SQL2016 named instance, which also hosts the source database.
The last item to specify is the backup file(s). Since a backup can span multiple files, I would need all the files listed here.
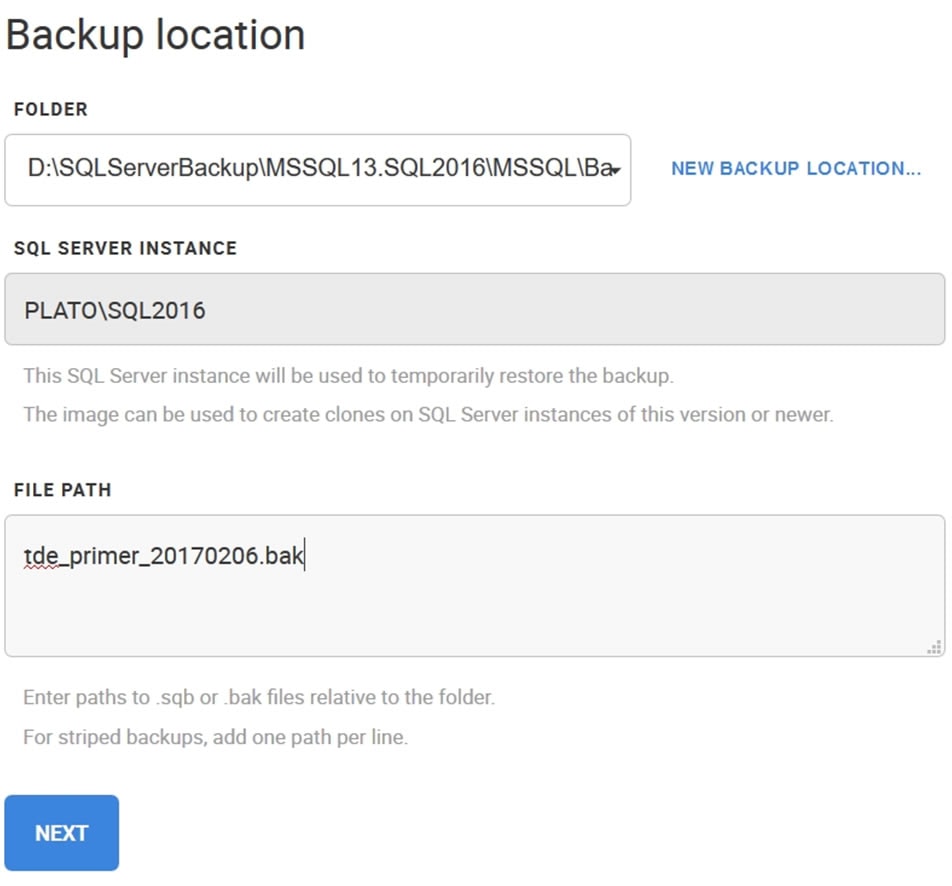
Figure 2
Now the form is filled, I click NEXT. I pick a destination for the image, which is a shared location that all of my SQL Clone agents can access.
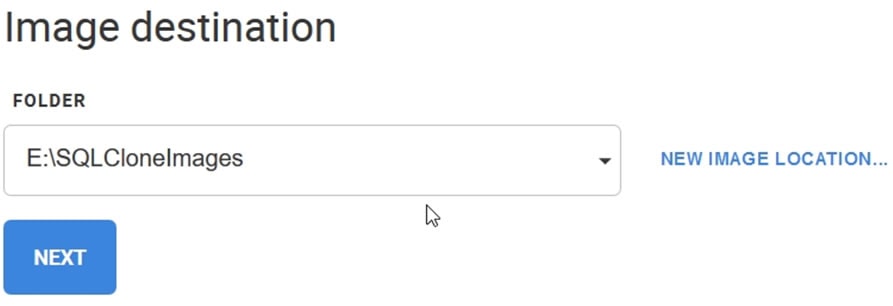
Figure 3
Once I do this, I give the image a name and review my choices.
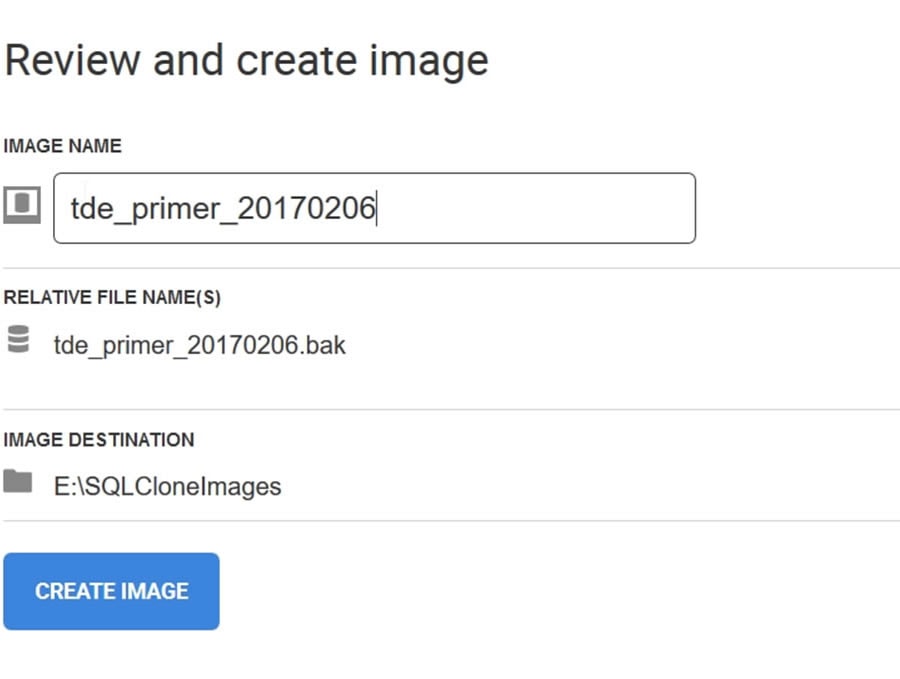
Figure 4
Click CREATE IMAGE and the image creation runs. As you can see, SQL Clone creates a temporary database on my instance in order to perform the restore:
Figure 5
The process completes, and I have an image. Adding a clone follows the same steps as described in the previous article, so I won’t go over them again here.
Creating a data image on a separate instance
What if we need to create a data image from a TDE-protected backup, but use a different instance for the restore process? In this case, I need to add a new backup location and associate this with a new instance.
To do this, I’ll click New Backup Location when I start to create a new image. I fill out the location and instance. I copied the same TDE-protected backup file that we used previously to this location.
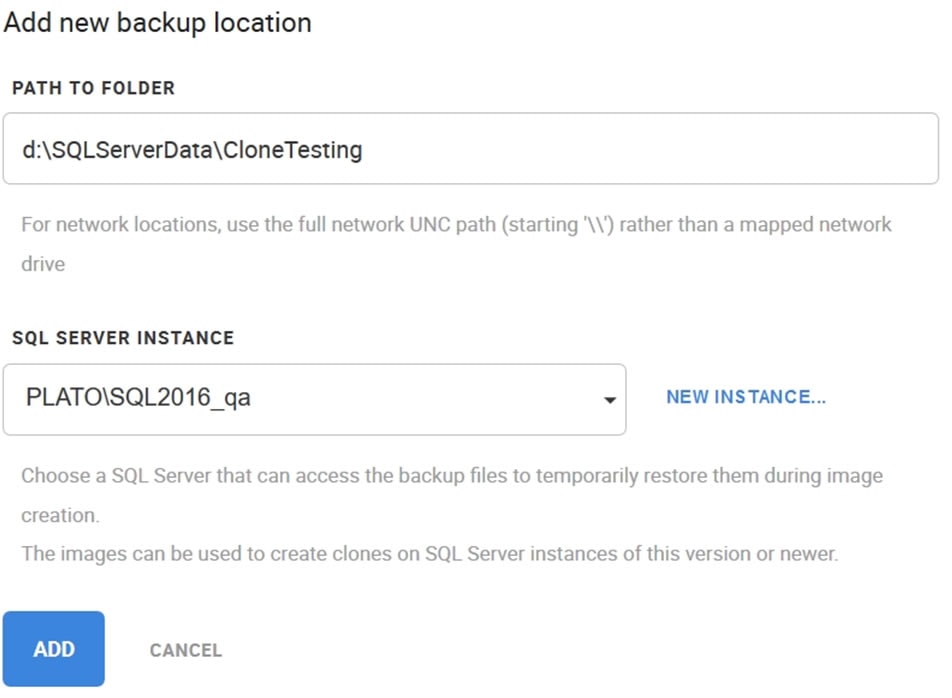
Figure 6
Now we can use the backup file to create the image. I’ll select the same image location, and then enter the image name. My settings look the same as before, though this restore is using a different instance.
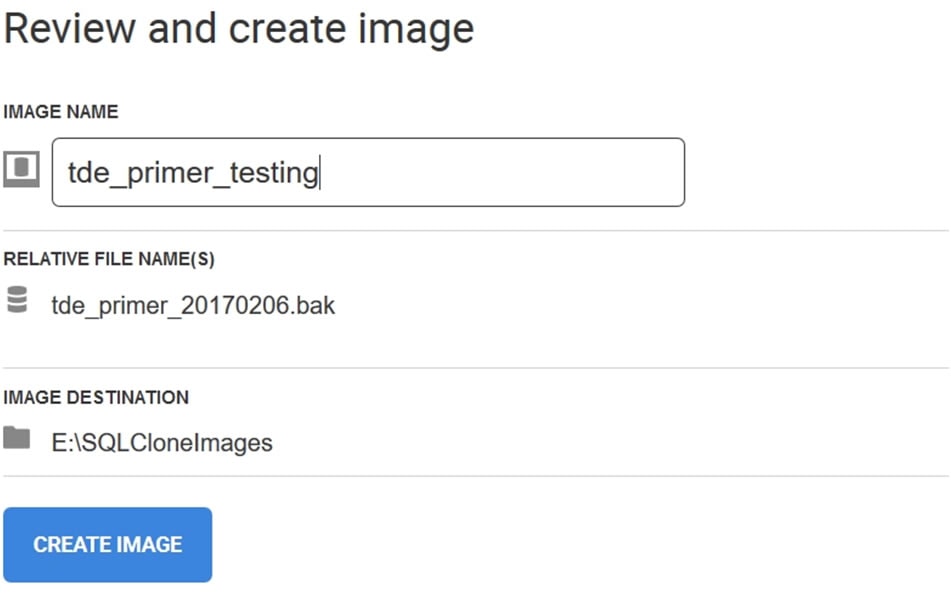
Figure 7
On this instance, however, I don’t have the certificate that protects my TDE database.
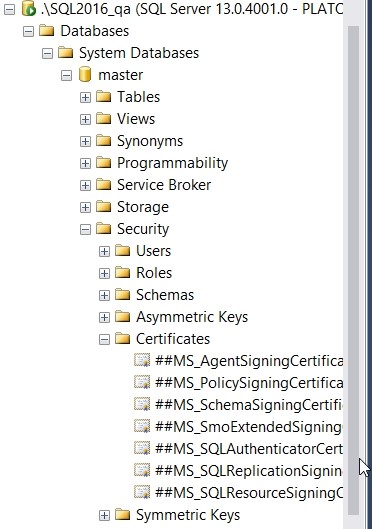
Figure 8
I would assume this means the restore can’t take place and therefore that the image won’t be created. So, what happens when I click CREATE IMAGE? As expected, I get a server thumbprint error.
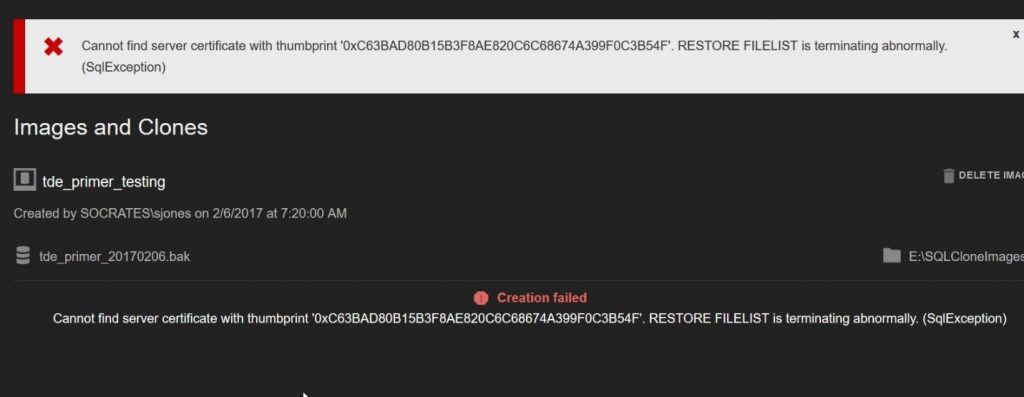
Figure 9
This is expected behavior when restoring a TDE-encrypted backup. I need the server certificate in order to decrypt the DEK and then read my encrypted data. I’ll restore the certificate as I did in the first article. Once I do that, I’ll see my server certificate in master.
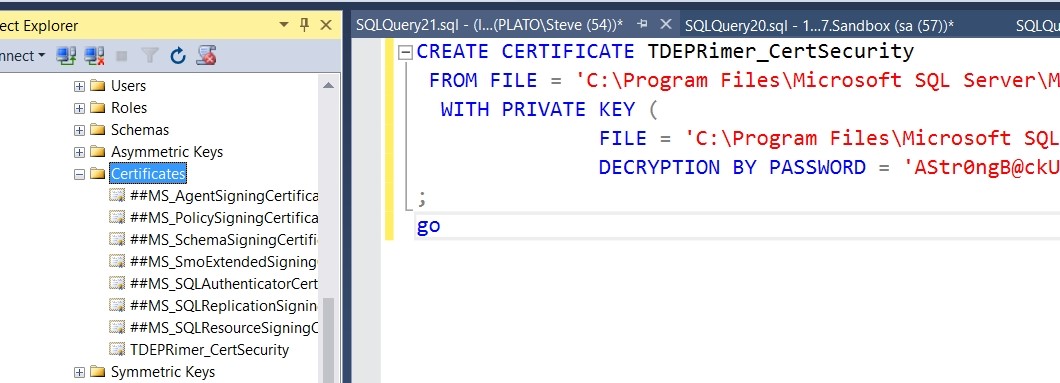
Figure 10
I can restart my image creation process, and this time it runs.
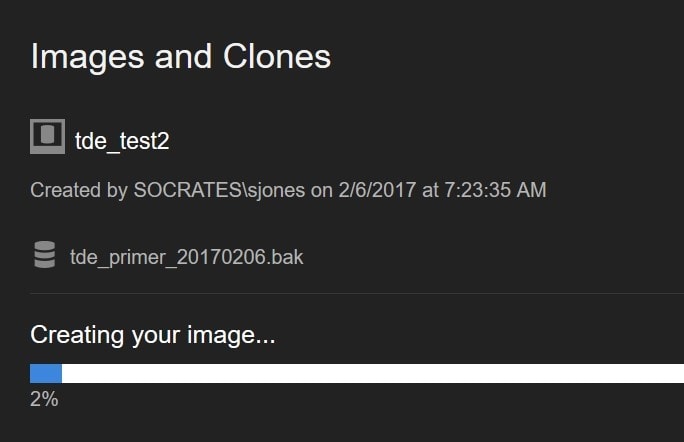
Figure 11
No error, my image is created, and I see it in my list in the dashboard.
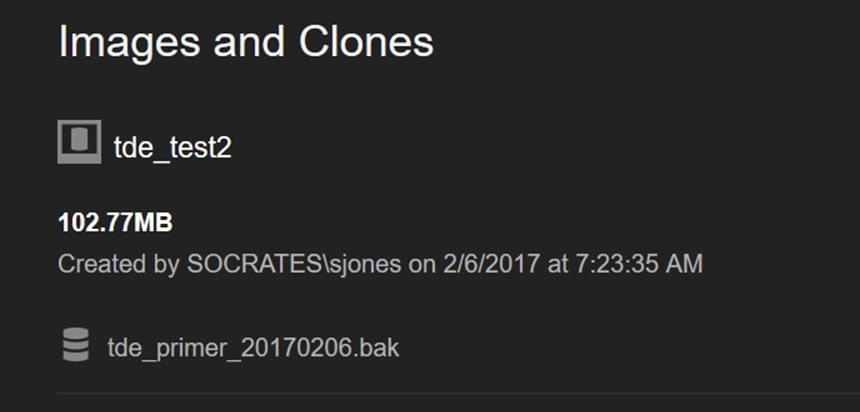
Figure 12
I can then create clones from this new image, just as I did in the first article.
SQL Clone and TDE ‘just works’
TDE is a great feature that provides a layer of security. It’s fairly simple, and easy to implement. It is also easy to move TDE databases across servers, if you understand how to move a certificate.
As you can see, SQL Clone builds on the SQL Server platform, and integrates nicely with TDE, provided you have the certificates created on the instances where you need to build images or SQL Clone databases.
Tools in this post
SQL Provision
Provision virtualized clones of databases in seconds, with sensitive data shielded



